Share:
-
Beginner
-
5 min read
-
Basics
In the Model Context Protocol (MCP), consent is the foundational security mechanism that governs how to delegate authority to AI agents. It ensures any actions they take are authorized, traceable, and revocable. Think of consent as a detailed, enforceable contract that spells out exactly what agents can do on the user’s behalf, going far beyond simple permissions.
tl;dr
Here’s what consent in MCP covers:
- Granular Delegation: Permissions are defined with a high degree of specificity. For example, an agent may be authorized to “send a specific email to a designated recipient” rather than having a general permission to “send emails to any contact.”
- Multi-layer Authorization: Security is enforced through multiple checkpoints, including agent identity verification, user authentication, MCP server access controls, and upstream service permissions.
- Explicit Scope: Every grant of permission clearly defines the delegator, the specific agent, and the exact purposes for which the authority is granted, thereby prohibiting overly broad or undefined permissions.
- Revocability and Auditability: Users retain the ability to revoke permissions at any time. All actions are logged to provide a clear and auditable trail of agent activity.
- Distributed Enforcement: The defined rules are consistently enforced across all components of the system, including MCP Hosts, Clients, and Servers, to ensure comprehensive security.
Note
Consent must be crystal clear, trackable, and enforceable. Otherwise, the door to unauthorized actions is wide open.
The core concept
A core principle of consent in MCP is that it must be explicit and specific, avoiding the ambiguity of a blanket acceptance of terms. The protocol requires a detailed definition of permissions, addressing the following questions:
- Who is delegating the authority?
- To which agent is the authority being delegated?
- For what purpose is the delegation being made?
This level of detail ensures clear lines of responsibility, which is particularly important in environments where multiple agents are operating concurrently.
Warning
Bypassing the explicit consent process can grant AI agents unrestricted access, which may lead to significant liability issues and an erosion of trust in the system.
Principles of consent
- Granularity: Get specific with permissions. Think “send an email to John about the budget meeting” instead of just “send emails,” which could lead to unintended outcomes.
- Revocability: You should be able to withdraw consent whenever you want, giving you control over your agents.
- Auditability: Everything is logged for later review, which is helpful when you need to understand why an agent took a specific action.
These principles help avoid classic security issues like the confused deputy problem, where an agent is tricked into misusing its authority.
Consent as a security control
Explicit consent serves as a primary defense against significant security vulnerabilities:
- Confused Deputy Attacks: This prevents servers from using the authority you granted for one purpose for a completely different one.
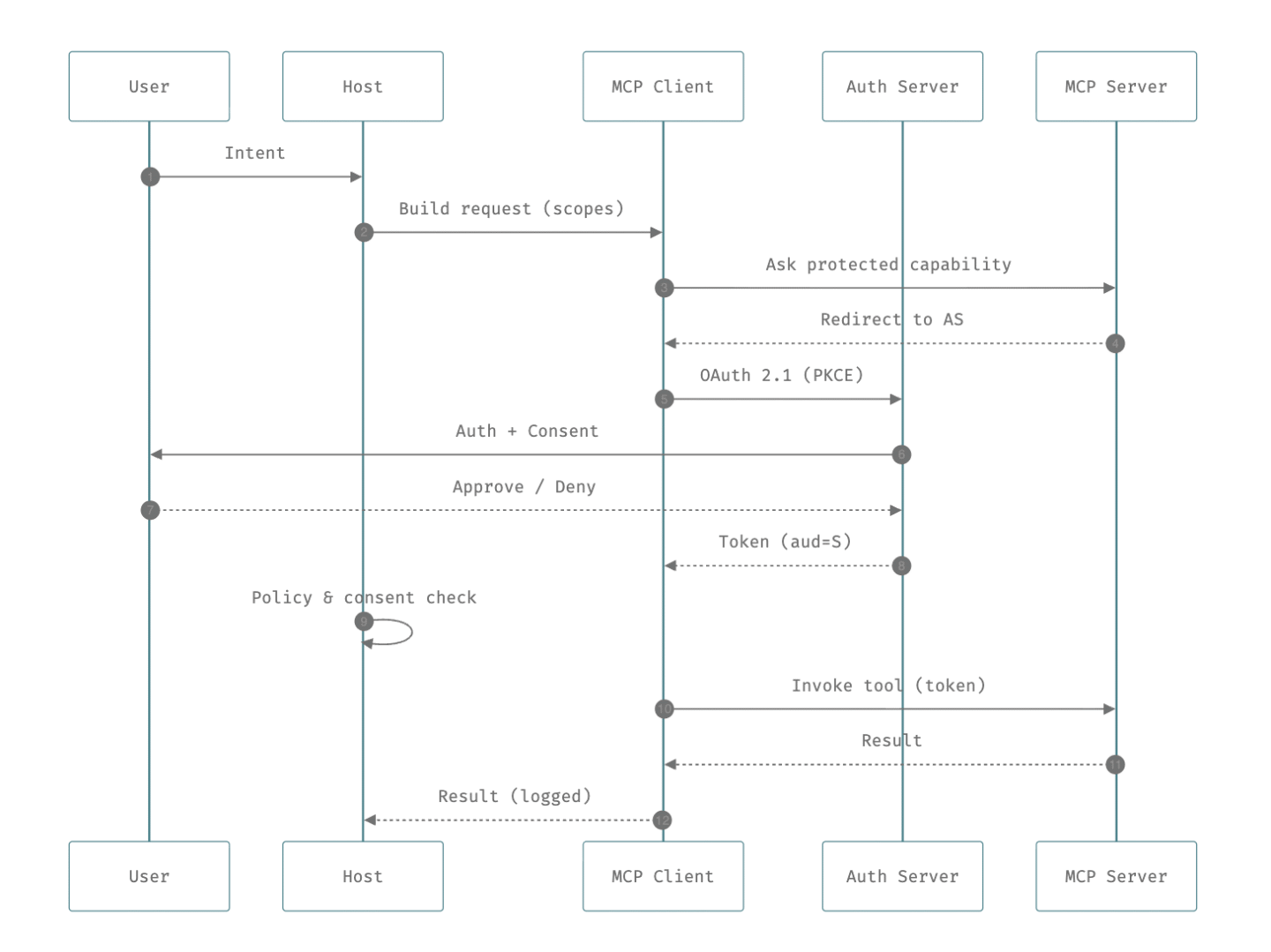
- Consent Bypass: The spec is clear: Hosts MUST get consent for every dynamically registered client before allowing third-party access. No exceptions [2]. This is critical for mitigating attacks where a previously granted consent cookie for a static client ID could be maliciously reused to authorize a new, attacker-controlled client without the user’s knowledge.
With strict scope enforcement, MCP seriously reduces the chances of agents performing unauthorized actions.
Conclusion
Consent in MCP is the foundation that keeps the system secure and accountable. With explicit, granular, and auditable permissions, it is possible to stay in control of what agents can do. This approach builds on the proven foundation of OAuth 2.1, extending it to protect against both classic web security threats and new AI-specific risks.
References
[1] Permit.io — The Ultimate Guide to MCP Auth